* 해당 포스팅은 플레인비트의 이준형 강사님의 강의를 듣고 작성한 스터디용 포스팅입니다.
Kali linux에서 Volatility download 및 python2 세팅
https://netsidetech.ca/2021/02/07/how-to-install-volatility-in-kali/
< 메모리 덤프 파일 분석하기 >
* 분석도구 - Volatility
* 분석 전 준비 사항
1. Volatility Tool 설치
1) python 2.7.13 버전 32비트로 설치 및 환경변수 (PATH) 설정 (Windows 7, 10 동일)
[그림 1-1 윈도우 환경 변수 설정]
파이썬 설치 후 (python 2.7.13) Pycrypto, PIL, Distorm3 설치
2) Pycrypto 설치 ( 32비트 ) : PyCrypto 2.6 for Python 2.7 32bit
3) PIL 1.1.7 : Python Imaging Library 1.1.7 for Python 2.7 (Windows only)
4) Distorm3 : distorm3-3.3.0.win32.exe (md5) 설치
2. Volatility 명령어
1) 이미지 프로파일 확인 명령어
> vol.py -f <image path> imageinfo
ex)
C:\volatility-master>python vol.py -f memory.2034161b.img imageinfo
Volatility Foundation Volatility Framework 2.4
Suggested Profile(s) : Win7SP1x64, WinXPSP3x86, Win2008R2SP0x64, Win20
08R2SP1x64, WinXPSP2x86, Win7SP0x64 (Instantiated with WinXPSP2x86)
AS Layer1 : FileAddressSpace (memory.2034161b.img)
PAE type : No PAE
DTB : 0x319000L
KDBG : 0x4dc5bce0L
Number of Processors : 0
Image Type (Service Pack) : 14731240
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 1970-01-01 00:00:00 UTC+0000
Traceback (most recent call last):
II. 프로파일 지정하여 메모리 덤프 분석
1) pstree

2) psscan

3) netscan

4) iehistory (인터넷 히스토리)

5) dumpfiles

6) memdump
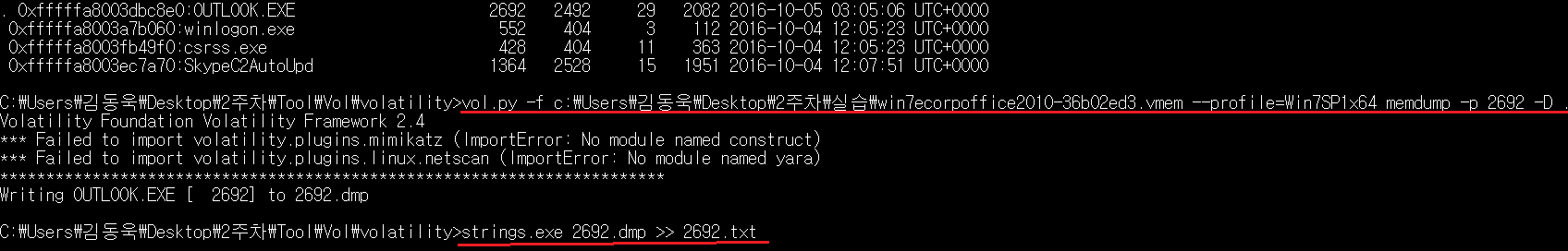
8) mftparser

9) filescan
ex) filescan | findstr "jpg"

* 실습 - 강사님이 제공한 .dump 파일에서 페이스북 계정 정보 추출하기
I. 이미지 프로파일 확인
>python vol.py -f "userinfo.dump" imageinfo
II. Strings 도구를 이용하여 문자열 추출
>strings -o "dump file path" > 파일명.txt
C:\Program Files (x86)\MANDIANT\Memoryze>strings -o "userinfo.dump" > userinfo_strings.txt
추출이 완료되면 Notepad++ 를 이용하여 open -> 문자열 검색
* 실습 2 (Challenge 1)
>python vol.py --profile=WinXPSP2x86 -f "메모리 덤프 파일" malfind -p 1640,1696
Volatility Foundation Volatility Framework 2.4
*** Failed to import volatility.plugins.dumpcerts (NameError: name 'yara' is not defined)
*** Failed to import volatility.plugins.linux.netscan (ImportError: No module named yara)
Process: IEXPLORE.EXE Pid: 1640 Address: 0x140000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 11, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x00140000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 MZ..............
0x00140010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0x00140020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00140030 00 00 00 00 00 00 00 00 00 00 00 00 c0 00 00 00 ................
0x140000 4d DEC EBP
0x140001 5a POP EDX
0x140002 90 NOP
0x140003 0003 ADD [EBX], AL
0x140005 0000 ADD [EAX], AL
0x140007 000400 ADD [EAX+EAX], AL
0x14000a 0000 ADD [EAX], AL
0x14000c ff DB 0xff
0x14000d ff00 INC DWORD [EAX]
0x14000f 00b800000000 ADD [EAX+0x0], BH
0x140015 0000 ADD [EAX], AL
0x140017 004000 ADD [EAX+0x0], AL
0x14001a 0000 ADD [EAX], AL
0x14001c 0000 ADD [EAX], AL
0x14001e 0000 ADD [EAX], AL
0x140020 0000 ADD [EAX], AL
0x140022 0000 ADD [EAX], AL
0x140024 0000 ADD [EAX], AL
0x140026 0000 ADD [EAX], AL
0x140028 0000 ADD [EAX], AL
0x14002a 0000 ADD [EAX], AL
0x14002c 0000 ADD [EAX], AL
0x14002e 0000 ADD [EAX], AL
0x140030 0000 ADD [EAX], AL
0x140032 0000 ADD [EAX], AL
0x140034 0000 ADD [EAX], AL
0x140036 0000 ADD [EAX], AL
0x140038 0000 ADD [EAX], AL
0x14003a 0000 ADD [EAX], AL
0x14003c c00000 ROL BYTE [EAX], 0x0
0x14003f 00 DB 0x0
Process: IEXPLORE.EXE Pid: 1696 Address: 0x140000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 11, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x00140000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 MZ..............
0x00140010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 ........@.......
0x00140020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00140030 00 00 00 00 00 00 00 00 00 00 00 00 c0 00 00 00 ................
0x140000 4d DEC EBP
0x140001 5a POP EDX
0x140002 90 NOP
0x140003 0003 ADD [EBX], AL
0x140005 0000 ADD [EAX], AL
0x140007 000400 ADD [EAX+EAX], AL
0x14000a 0000 ADD [EAX], AL
0x14000c ff DB 0xff
0x14000d ff00 INC DWORD [EAX]
0x14000f 00b800000000 ADD [EAX+0x0], BH
0x140015 0000 ADD [EAX], AL
0x140017 004000 ADD [EAX+0x0], AL
0x14001a 0000 ADD [EAX], AL
0x14001c 0000 ADD [EAX], AL
0x14001e 0000 ADD [EAX], AL
0x140020 0000 ADD [EAX], AL
0x140022 0000 ADD [EAX], AL
0x140024 0000 ADD [EAX], AL
0x140026 0000 ADD [EAX], AL
0x140028 0000 ADD [EAX], AL
0x14002a 0000 ADD [EAX], AL
0x14002c 0000 ADD [EAX], AL
0x14002e 0000 ADD [EAX], AL
0x140030 0000 ADD [EAX], AL
0x140032 0000 ADD [EAX], AL
0x140034 0000 ADD [EAX], AL
0x140036 0000 ADD [EAX], AL
0x140038 0000 ADD [EAX], AL
0x14003a 0000 ADD [EAX], AL
0x14003c c00000 ROL BYTE [EAX], 0x0
0x14003f 00 DB 0x0
>python vol.py --profile=WinXPSP2x86 -f "unpack.vmem" dlldump -p 1640,1696 --base=0x140000 -D ./
Volatility Foundation Volatility Framework 2.4
*** Failed to import volatility.plugins.dumpcerts (NameError: name 'yara' is not defined)
*** Failed to import volatility.plugins.linux.netscan (ImportError: No module named yara)
Process(V) Name Module Base Module Name Result
---------- -------------------- ----------- -------------------- ------
0x81eaf2c0 IEXPLORE.EXE 0x000140000 UNKNOWN OK: module.1640.22af2c0.140000.dll
0x81b222e0 IEXPLORE.EXE 0x000140000 UNKNOWN OK: module.1696.1f222e0.140000.dll
dll 파일의 시작점
CFF Exploerer.exe 파일 -> dll 파일 open -> optional header 클릭 -> imagebase 수정 및 save
00140000 으로.(dll 파일의 시작점, EBP)
immunity debugger 또는 올리디버거로 파일 오픈
immunity debugger -> 프로그램 상단의 'e' 클릭 -> 최상단 dll 파일 시작점 00140000
더블클릭-> 실행 줄이 나오면 마우스 우클릭 -> search for -> all referenced for strings
확인.
시작점이 ntdll 로 되어있다 .
e 를 클릭하는 것은 맨 위 시작점으로 가는 것이다.
Challenge 1 실습 리뷰
>python vol.py -f "Bob.vmem" imageinfo
Volatility Foundation Volatility Framework 2.4
*** Failed to import volatility.plugins.dumpcerts (NameError: name 'yara' is not defined)
*** Failed to import volatility.plugins.linux.netscan (ImportError: No module named yara)
INFO : volatility.plugins.imageinfo: Determining profile based on KDBG search...
Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86)
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : FileAddressSpace (Bob.vmem)
PAE type : PAE
DTB : 0x319000L
KDBG : 0x80544ce0L
Number of Processors : 1
Image Type (Service Pack) : 2
KPCR for CPU 0 : 0xffdff000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2010-02-27 20:12:38 UTC+0000
Image local date and time : 2010-02-27 15:12:38 -0500
>python vol.py -f "Bob.vmem" pstree
>python vol.py --profile=WinXPSP2x86 -f "Bob.vmem" connections
Volatility Foundation Volatility Framework 2.4
*** Failed to import volatility.plugins.dumpcerts (NameError: name 'yara' is not defined)
*** Failed to import volatility.plugins.linux.netscan (ImportError: No module named yara)
Offset(V) Local Address Remote Address Pid
---------- ------------------------- ------------------------- ---
0x81c6a9f0 192.168.0.176:1176 212.150.164.203:80 888
0x82123008 192.168.0.176:1184 193.104.22.71:80 880
0x81cd4270 192.168.0.176:2869 192.168.0.1:30379 1244
0x81e41108 127.0.0.1:1168 127.0.0.1:1169 888
0x8206ac58 127.0.0.1:1169 127.0.0.1:1168 888
0x82108890 192.168.0.176:1178 212.150.164.203:80 1752
0x82210440 192.168.0.176:1185 193.104.22.71:80 880
0x8207ac58 192.168.0.176:1171 66.249.90.104:80 888
0x81cef808 192.168.0.176:2869 192.168.0.1:30380 4
0x81cc57c0 192.168.0.176:1189 192.168.0.1:9393 1244
0x8205a448 192.168.0.176:1172 66.249.91.104:80 888
>python vol.py --profile=WinXPSP2x86 -f "Bob.vmem" memdump -p 888 -D ./
Volatility Foundation Volatility Framework 2.4
*** Failed to import volatility.plugins.dumpcerts (NameError: name 'yara' is not defined)
*** Failed to import volatility.plugins.linux.netscan (ImportError: No module named yara)
************************************************************************
Writing firefox.exe [ 888] to 888.dmp
>python vol.py --profile=WinXPSP2x86 -f "Bob.vmem" memdump -p 1752 -D ./
Volatility Foundation Volatility Framework 2.4
*** Failed to import volatility.plugins.dumpcerts (NameError: name 'yara' is not defined)
*** Failed to import volatility.plugins.linux.netscan (ImportError: No module named yara)
************************************************************************
Writing AcroRd32.exe [ 1752] to 1752.dmp
실습 - Challenge 2
>python vol.py --profile=WinXPSP2x86 -f "windows_xp_pro.vmem" pstree
>python vol.py --profile=WinXPSP2x86 -f "windows_xp_pro.vmem" screenshot -D ./
'DFIR' 카테고리의 다른 글
| <실습-1 : 성인 포렌식 케이스> (0) | 2019.02.08 |
|---|---|
| FireEye NX 이벤트 분석 예시 (0) | 2019.02.08 |
| [윈도우 포렌식 실전 가이드] 2장 소프트웨어 덤프 (0) | 2017.07.03 |
| [윈도우 포렌식 실전 가이드] 1장_라이브 리스폰스 스크립트 (0) | 2017.06.30 |
| Cuckoo Sandbox 2.0설치 - for Windows 7 (0) | 2017.02.23 |